-
Notifications
You must be signed in to change notification settings - Fork 41
How to get A plus on Qualys SSL Labs Test
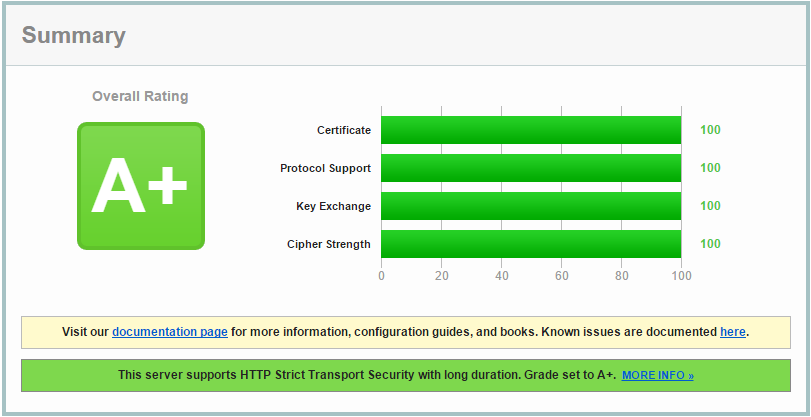
For this exercise, we’ll throw compatibility with older operating systems and browsers out and only focus on maxing out security.
First, we need a 4096 bit private key. In the following, replace “your.domain” with the real domain name you’re going to protect.
openssl genrsa -out your.domain.key 4096
openssl req -sha256 -new -key your.domain.key -out your.domain.csr
Your private key is in the file your.domain.key. The file your.domain.csr contains your certificate signing request, which needs to be sent to your certification authority. The details of that procedure is different depending on the CA, but should result in you having your new certificate in your possession. Save the certificate as your.domain.crt.
The final piece of information you need is the CA’s certificate, which the CA will provide. Save the certificate as intermediate.crt.
Assuming you managed to cobble together all these files in the directory /etc/pen, the certificate installation is now finished.
This is easy. Nobody supports SSL 2.0 anymore. SSL 3.0 is only for IE6 on Windows XP, a dwindling user base. TLS 1.0 is still acceptable, but this is not an exercise in acceptability (or compatibility). Throw out everything but TLS 1.2 by putting the following in /etc/pen/https.cfg:
ssl_option no_sslv2
ssl_option no_sslv3
ssl_option no_tlsv1
ssl_option no_tlsv1.1
We want ECDHE support for perfect forward secrecy, we want 256 bits encryption, and we want to prefer the best ciphers. These lines in /etc/pen/https.cfg provide that:
ssl_ciphers ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:kEDH+AESGCM:ECDHE-RSA-AES256 SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES256-GCM-SHA384:AES256-SHA256:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK
ssl_option cipher_server_preference
The final piece of the puzzle is HSTS, which we accomplish by putting this in our Apache config:
Header always set Strict-Transport-Security "max-age=63072000; includeSubdomains; preload"
Finally, enable mod_headers and restart Apache:
a2enmod headers
service apache2 restart
The command line for Pen looks like this:
/usr/local/bin/pen -u pen -C /var/run/pen/https.ctl -F /etc/pen/https.cfg -p /var/run/pen/https.pid -K /etc/pen/your.domain.key -E /etc/pen/your.domain.crt -G /etc/pen/intermediate.crt -S 2 443
That’s quite a bit to type. If you’re using Systemd, like the CentOS system that was used for this example, here’s the full unit file to be installed into /usr/lib/systemd/system:
[Unit]
Description=Pen load balancer (https)
[Service]
Type=forking
PIDFile=/var/run/pen/https.pid
ExecStart=/usr/local/bin/pen -u pen -C /var/run/pen/https.ctl -F /etc/pen/https.cfg -p /var/run/pen/https.pid -K /etc/pen/your.domain.key -E /etc/pen/your.domain.crt -G /etc/pen/intermediate.crt -S 2 443