-
Notifications
You must be signed in to change notification settings - Fork 108
SSL Certificate Validation with ADFS
When you try to authenticate by using the Azure Active Directory Authentication Library (ADAL) for Android or Microsoft Authentication Library for Android (MSAL), Federation sign-in may fail. Specifically, the application triggers an AuthenticationException error when it tries to display the login page. In Google Chrome, the STS login page might be called out as unsafe. This issue occurs only on Android devices, for any application that uses ADAL for Android to connect to a Federation server.
E BasicWebViewClient: ERROR_FAILED_SSL_HANDSHAKE:2017-09-29 14:22:24-<GUID>-Received ssl error ver:1.12.0
Error info:Code:-11 primary error: 3
Certificate: Issued to: CN=*.<sometext>.<some text.com>,OU=<some text>,O=<some text>,C=FR;
Issued by: CN=Symantec Class 3 Secure Server CA - G4,OU=Symantec Trust Network,O=Symantec Corporation,C=US;
- Get the URL for the ADFS instance
- Format is typically a domain with a path ending in
/adfs/ls - Example:
https://sts.contoso.com/adfs/ls
- Format is typically a domain with a path ending in
- Run a Qualsys SSL Server Test
- Review the report
- Did the domain receive a failing grade for any reason?
- Is the cert chain incomplete?
- Are there 'Extra Download' certificates?
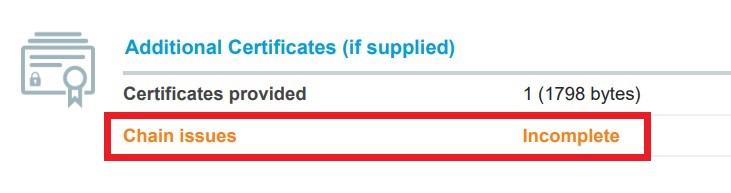
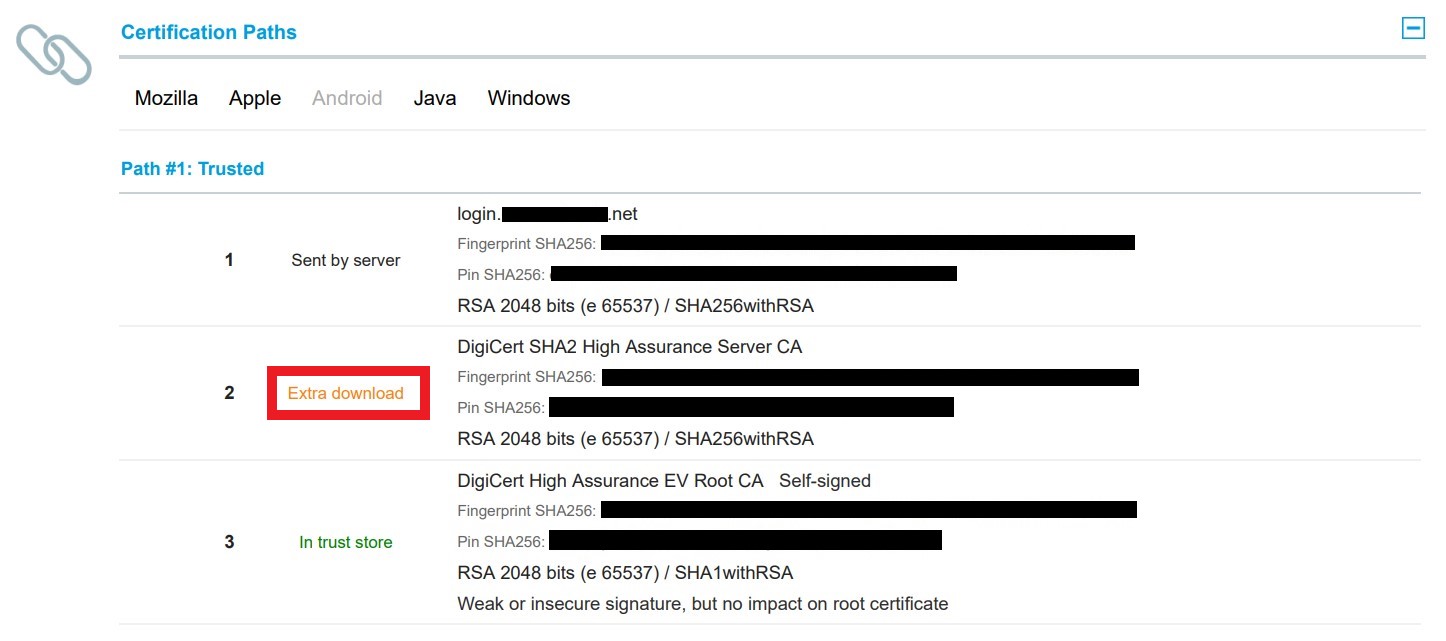
- Typically, this issue must be resolved by an IT admin for the affected tenant or domain.
- End-users facing this issue are advised to reach out to their IT admin, providing the relevant Qualsys SSL report to assist in troubleshooting
- If contacting Microsoft, include the same information as appropriate
- For more information, see MS Docs
A number of potential SSL issues are captured by Code:-11 primary error: 3; the below list outlines common issues.
- Intermediate "Extra Download" Certificates
- Android does not support downloading additional certificates from the
authorityInformationAccessfield of the certificate. This is true across all Android versions and devices, and for the Chrome browser. Any server authentication certificate that's marked for extra download based on theauthorityInformationAccessfield will trigger this error if the entire certificate chain is not passed from Active Directory Federation Services (AD FS).
- Android does not support downloading additional certificates from the
- Network Firewalls, Proxies, Packet Filtering Appliances
- In order to maintain a secure channel while authenticating users, ADAL validates the certificate chain of the STS. If the the chain cannot be validated or is determined to be invalid, authentication is not performed and neither tokens nor credentials are sent over the insecure channel.
- Proxies such as Charles, Fiddler, and others may be configured to intercept and sniff "secure channel" traffic; this is often accomplished by injecting intermediate certificates into the trust-chain. These certificates are untrusted by default and will not be accepted as a valid link in the trust chain unless installed into the Android device's certificate store**. Consult your IT administrator/personnel as necessary to resolve SSL issues related to proxy configuration or to request the necessary certificate for your device.
** Note: The exact mechanism for validating certificate trust chains varies across devices, manufacturers, and OS versions. Some users have reported issues when debugging using proxies such as Fiddler; if you have specific questions or feedback on this point, please file an issue..
- Error Handling
- Auth Telemetry
- Logging
- Doze and App Standby
- ProGuard
- Session Cookies in WebView
- Resource Overrides